A Keylogger is software you install on a computer to spy on family, friends, or employees. Keyloggers work by tracking and logging every keystroke, website, and action that someone does on a computer under your control. You can periodically send those logs to your email or review them manually on the computer when your target is not around.
Who Would Need A Keylogger?
Keyloggers are popular with hackers because they can trick you into installing them so that they can steal your passwords or see the sites that you visit without you being aware. However, current anti-virus programs know keyloggers, making them difficult to install for legitimate purposes.
So why would a non-hacker want to use a keylogger application?
- Is your significant other acting suspiciously? Are they cheating on you?
- Are your employees stealing from you by wasting time surfing the Internet all day?
- Are your kids watching inappropriate things online or chatting with the wrong people?
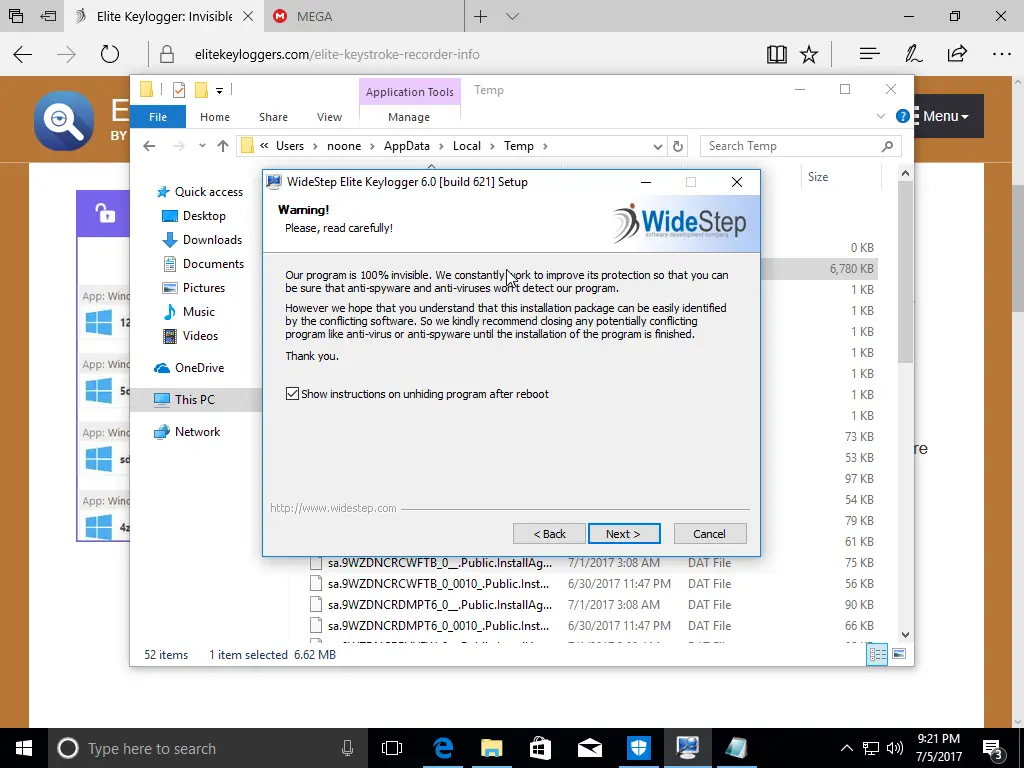
There are several valid reasons for installing a keylogger on your computer, but please be aware that this will not be easy if you’re not very good with computers. They make it easy for you and offer support on their website.
Keyloggers also represent a moral gray area with potential legal consequences if misused. Please review your local laws about installing keyloggers.
Elite Keylogger for Windows or Mac
In this review, we tried out Elite Keylogger for Windows. We installed it on a new Windows 10 Pro virtual machine without third-party security or anti-virus plugins. Windows Defender was enabled by default. If you need a Mac version, please click here.
Installation
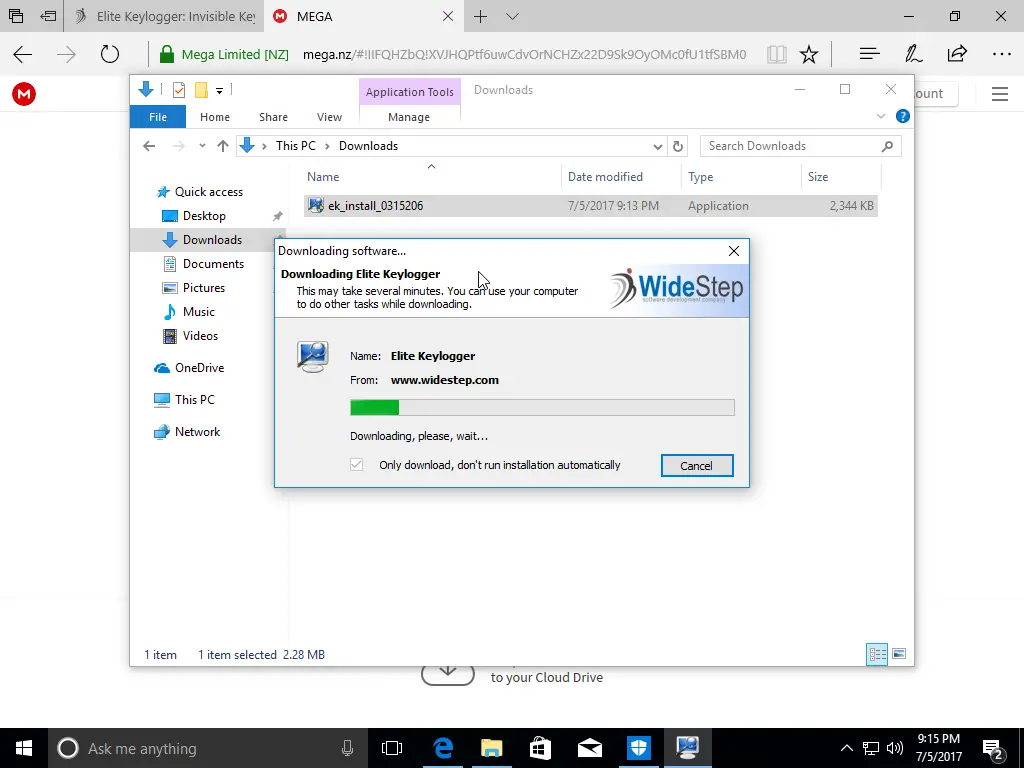
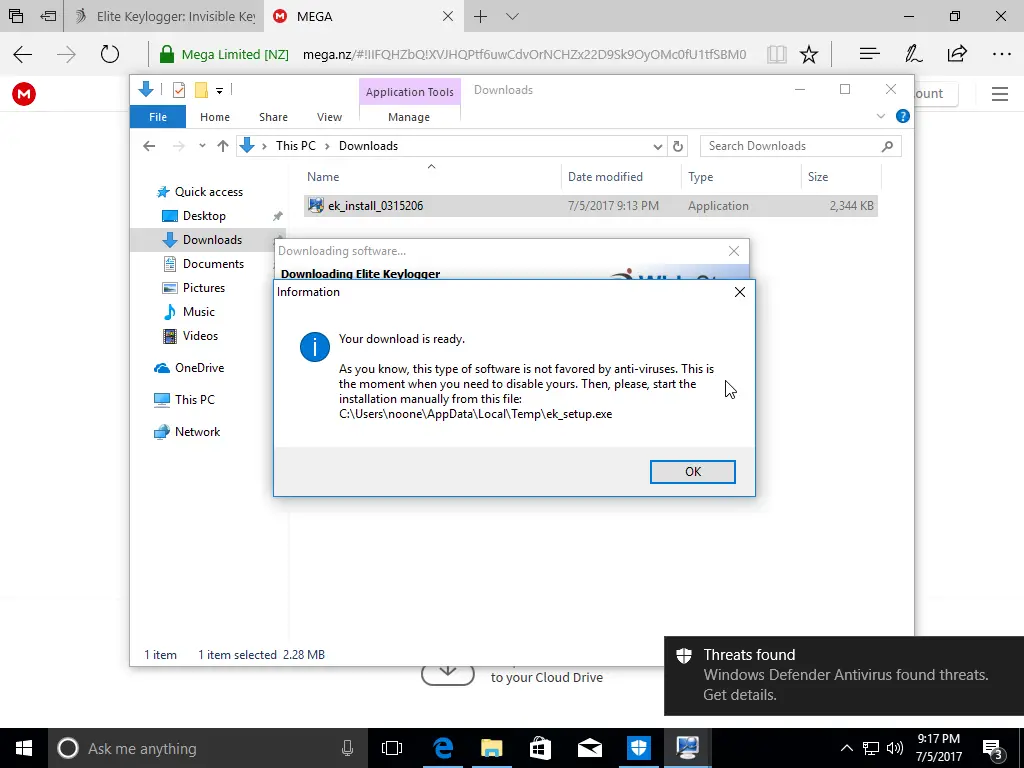
To install the software, you have to download a small file from mega.nz by copying a link and then pasting it into another tab or browser. The default is to download for Mac OS, so switch it to the “For Windows” tab.
This small file (ek_install_0315206.exe) is later downloaded to download the actual software (ek_setup.exe).
Before you download, you’ll see a warning, “It’s your sole responsibility to make sure your local laws any [sic] digital surveillance and using a keylogger is legal in your country.”
By the way, they say that their software will work on Windows XP, and we initially tried to download it on our trusty old Windows XP virtual machine; however, you won’t be able to download it from their site because IE is not able to connect to websites with newer SSL certificates (HTTPS).
But if you’re still using Windows XP, you have more significant problems than a cheating boyfriend!
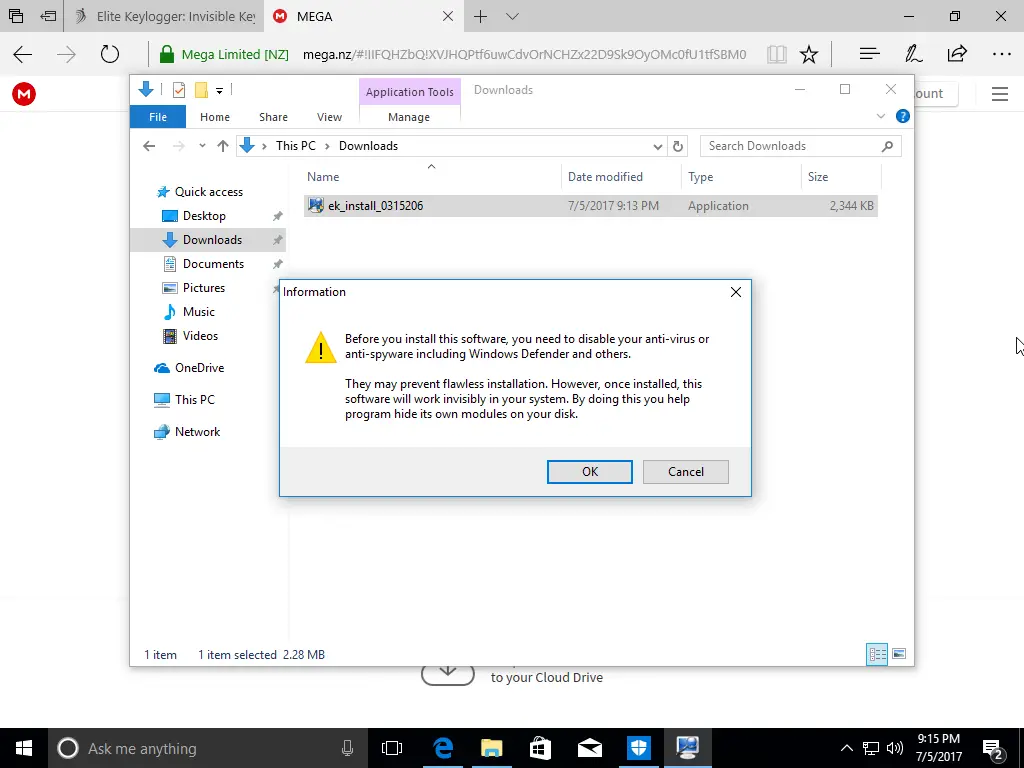
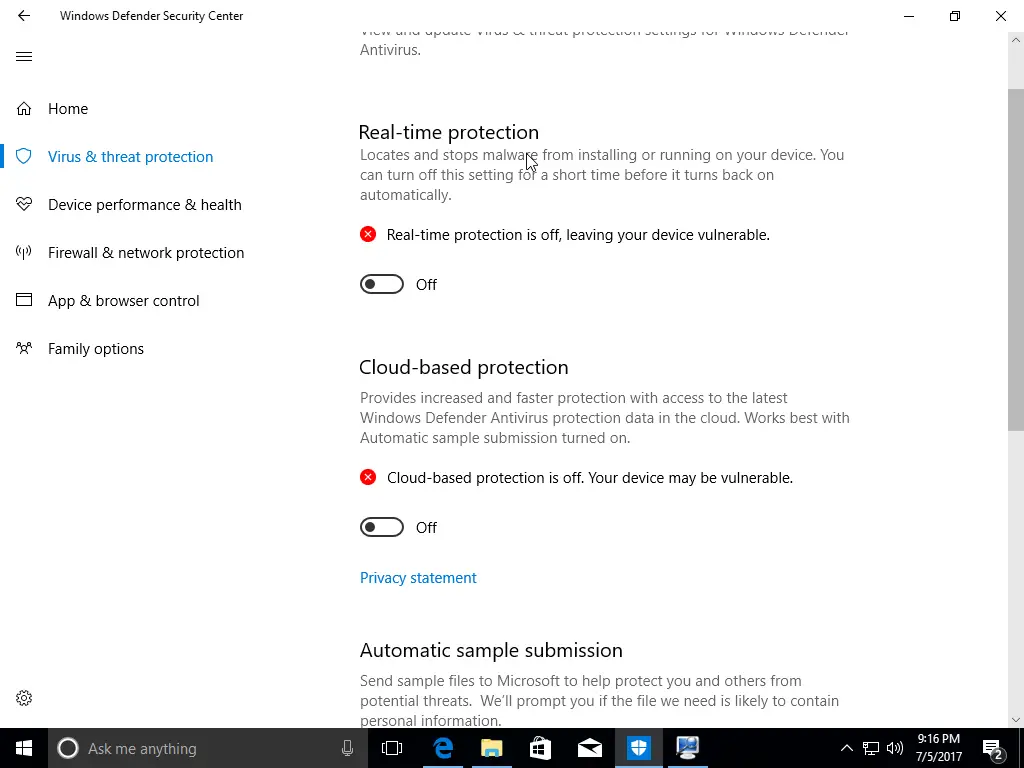
Disable Anti-Virus Protection
Before you continue, you should review some of the warnings that you will get when you try to install their keylogger: https://www.keylogger.org/monitoring-software-review/elite-keylogger.html
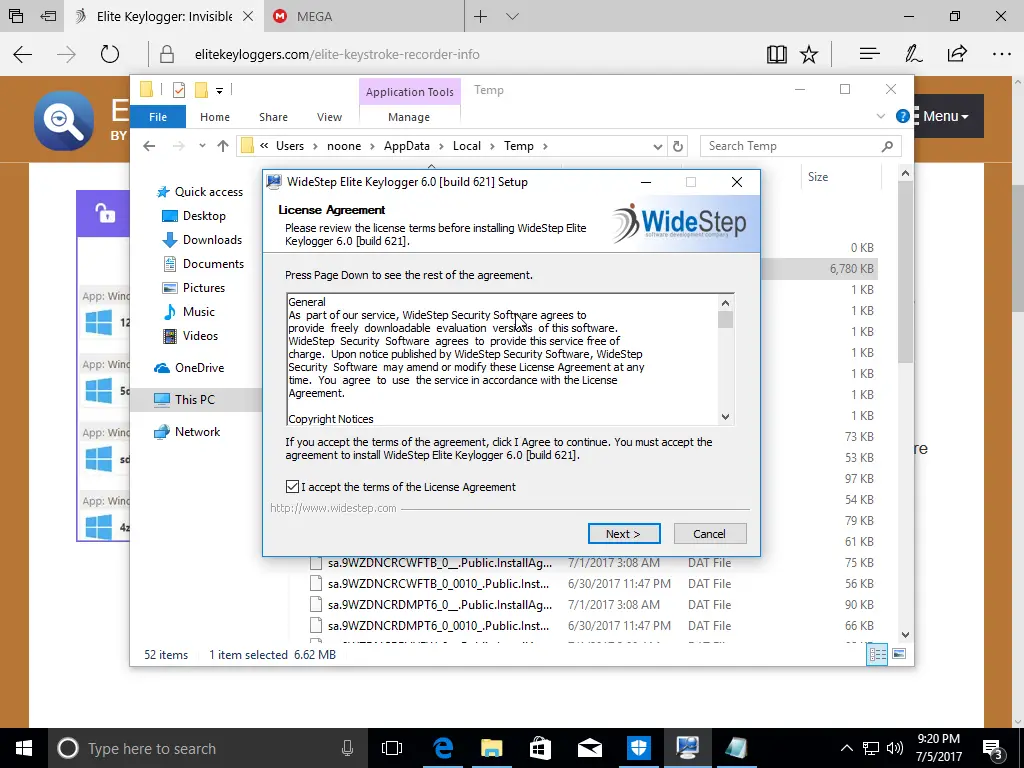
Some of the statements sound questionable. It’s what a scammer would say to you to try and convince you to fall for their scam. But keyloggers are technically malware, and to pull this off, you will have to go a bit further than just installing it and waiting for your target to use the machine.
If you’re using a Mac, you probably don’t have as much to disable since Macs usually don’t have any virus software installed.
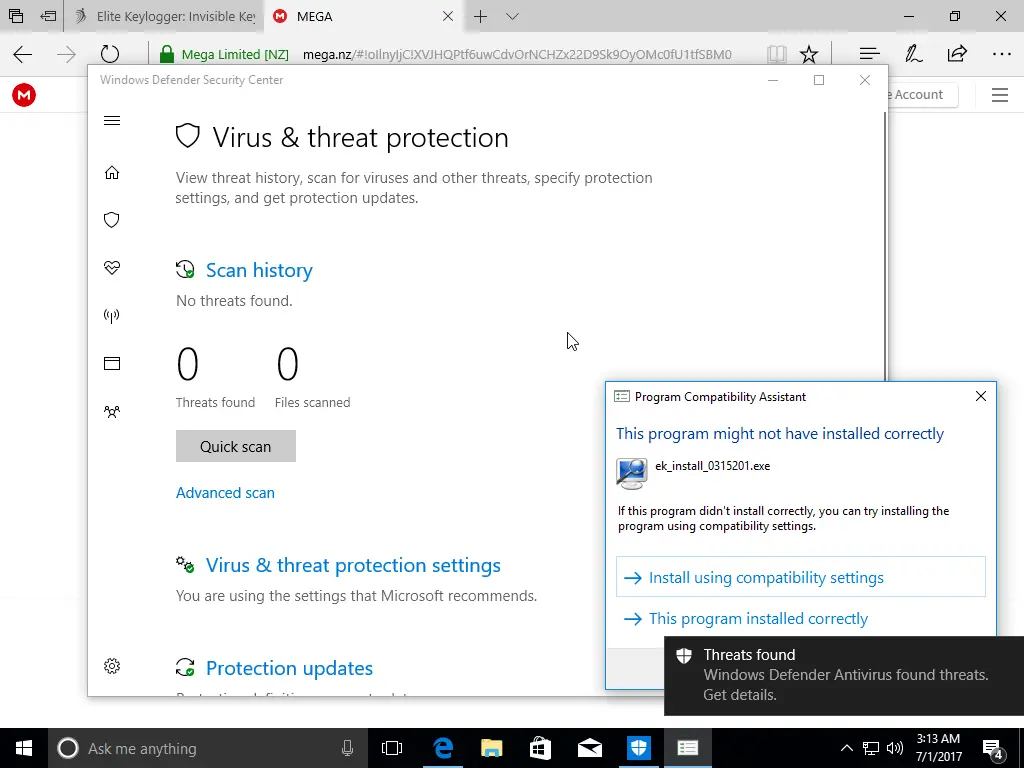
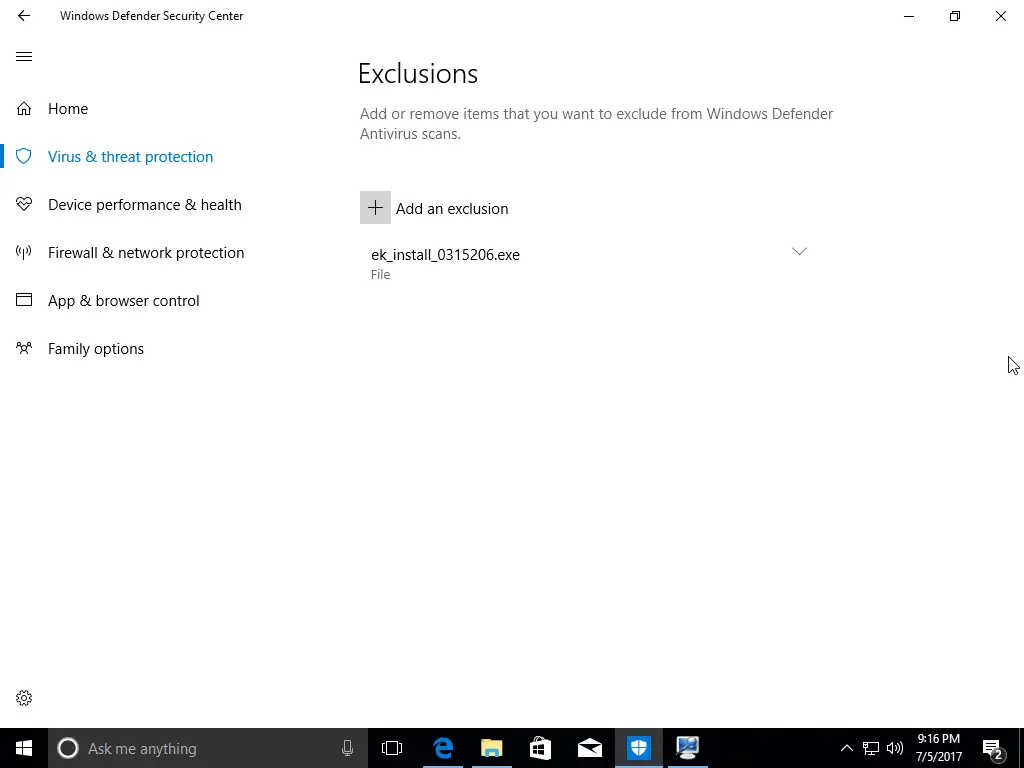
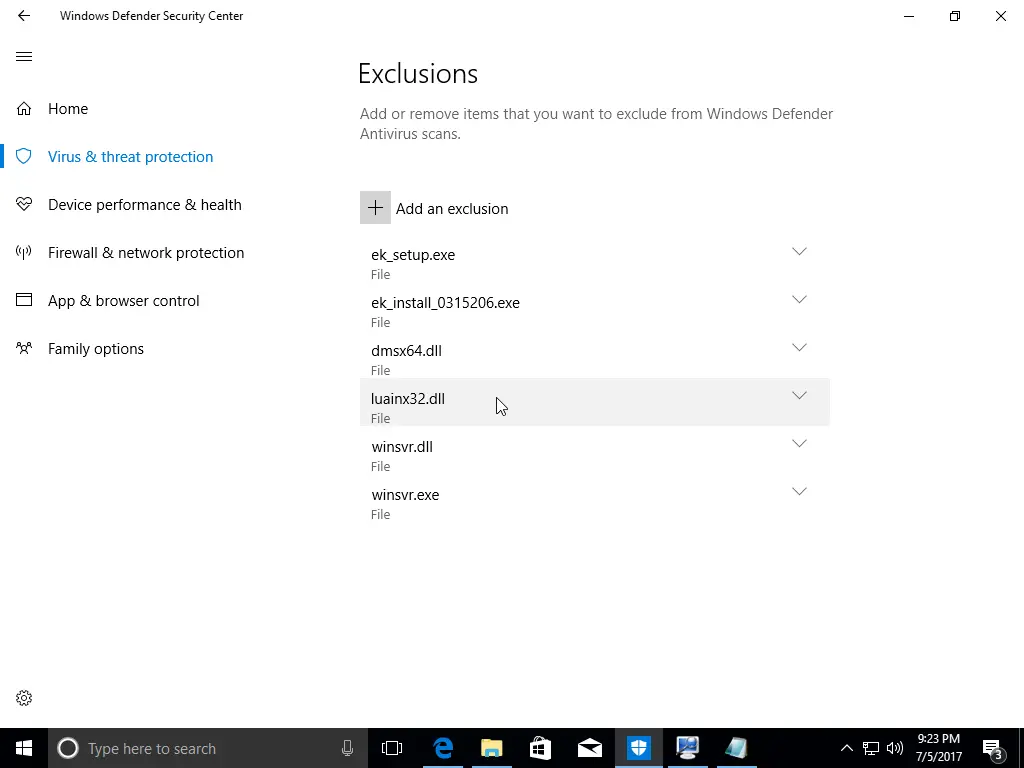
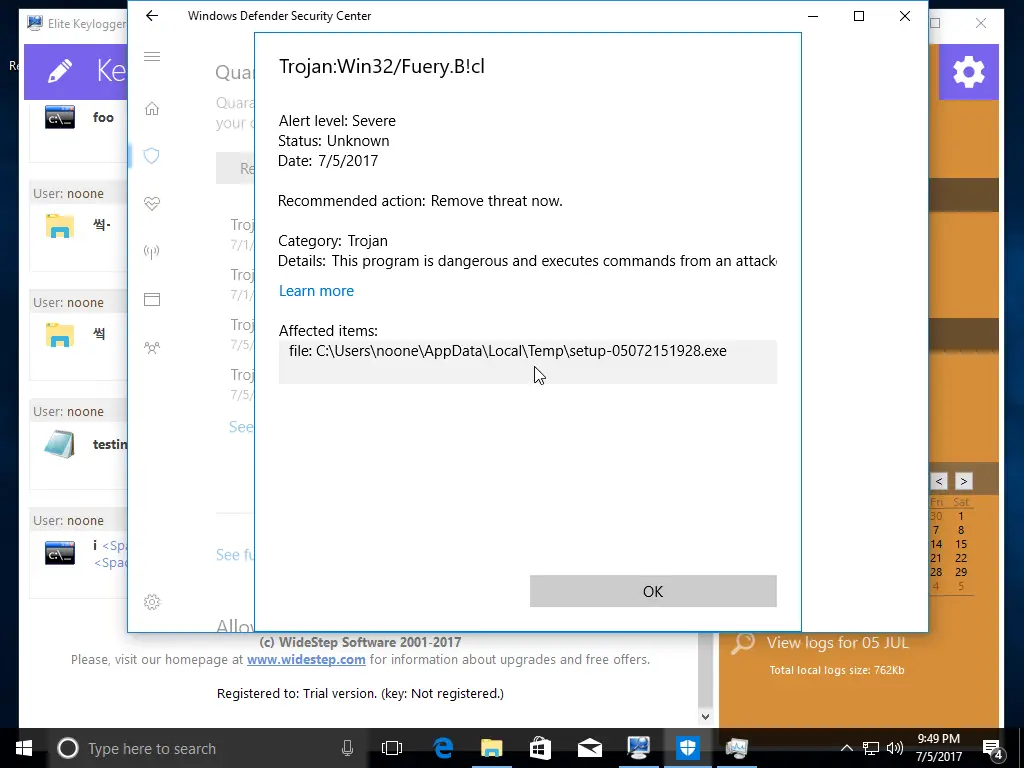
After downloading the initial file, we almost immediately got a warning from Windows Defender about a virus. We took a lot of screenshots, so check out the gallery below to see what happened. We disabled Windows Defender’s Real-time protection and Cloud-based protection. Before being prompted (see gallery), we added the two downloaded files to our exclusions list to help prevent any further difficulties.
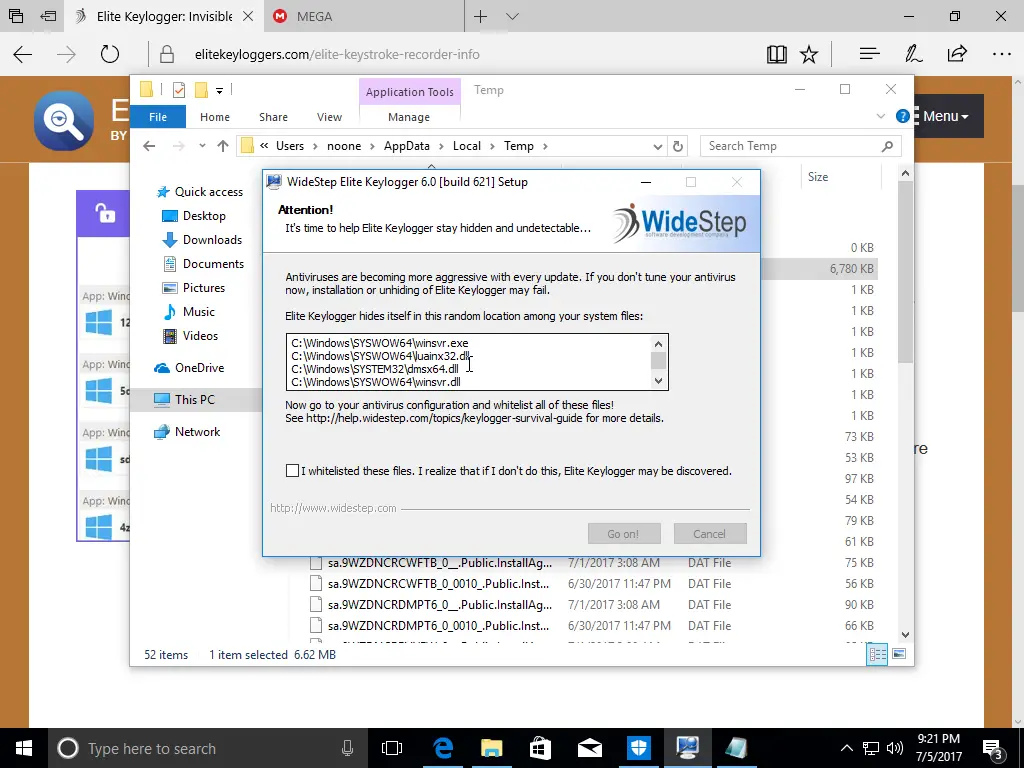
Continuing with the installation, the software told us to add four files to our anti-virus exclusions list. If you don’t know how to disable your anti-virus, you’ll probably have difficulty finding where to add exclusions. Again, we’re not going to go over how to add exclusions to your favorite anti-virus software, but if you poke around the options and settings long enough, you’ll likely find it.
Post Installation Options
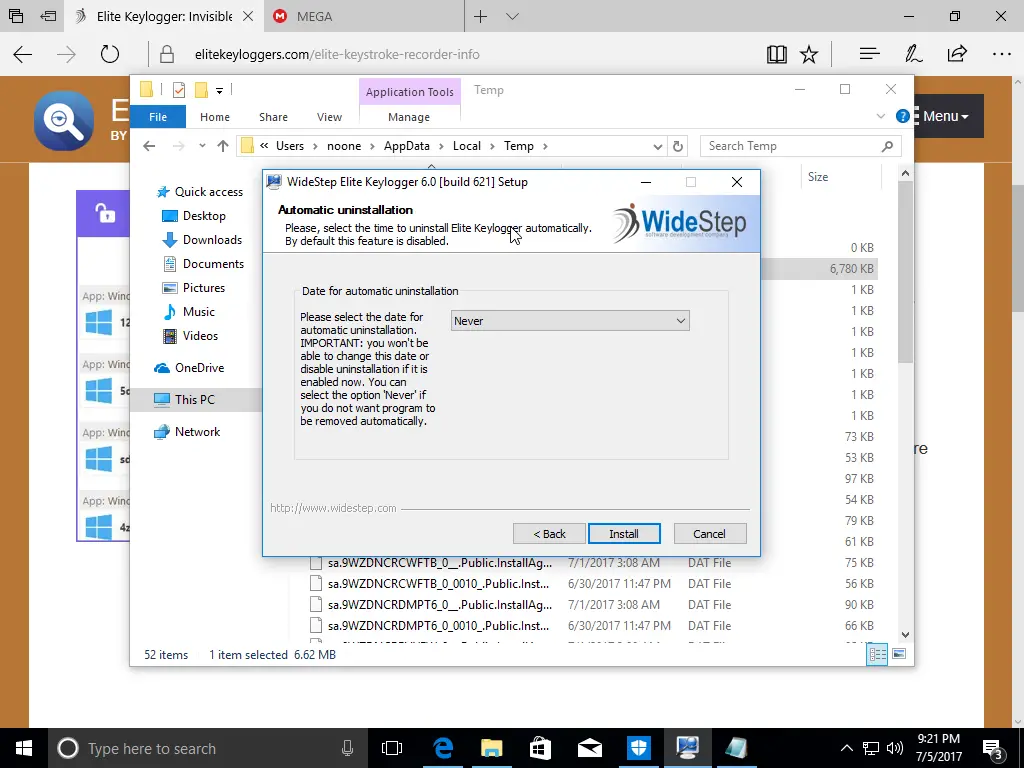
During the installation, you have some decisions to make. If you only want to monitor the target briefly, you can schedule the software to delete itself automatically. That was a nice, unexpected feature.
Super Secret Key
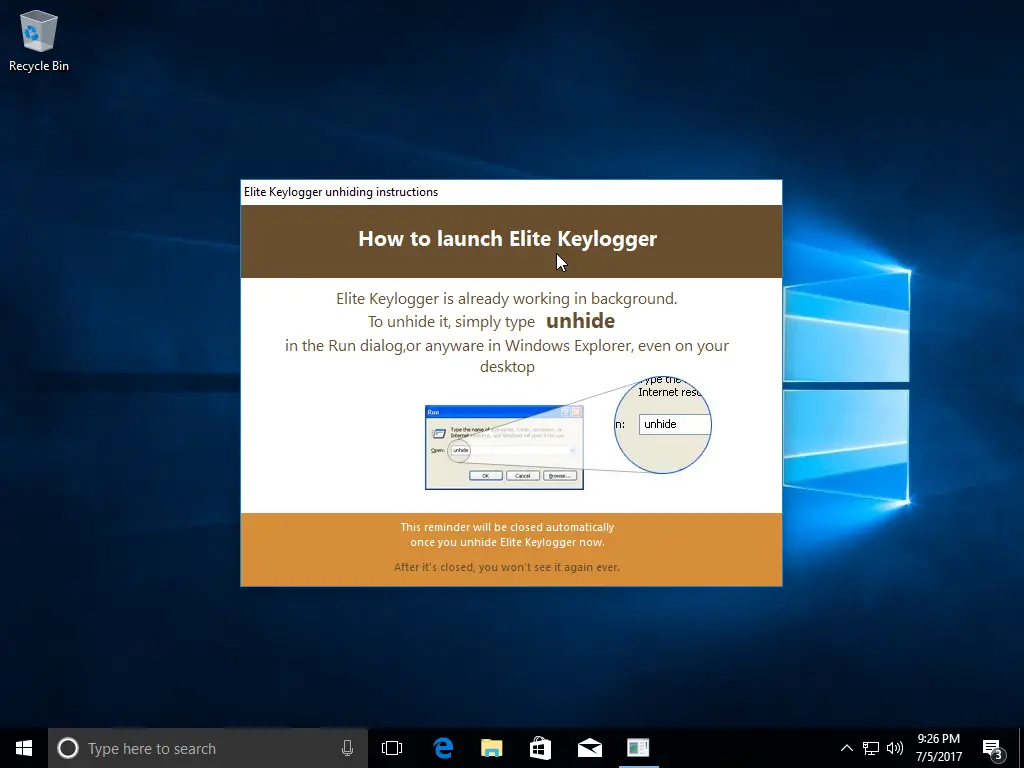
Moving forward in time a bit…after you install and configure the software, you will need to close it so that your target can’t see it, right? But how do you return to make changes or see what your target was doing?
Once you install the software, you have to type a super secret word into your Run menu to open it. That super secret word? “unhide”
If you’re monitoring your employees and you have a particularly savvy computer programmer on your staff, you might want to change the secret word to something else. Luckily, the software allows you to change “unhide” to whatever you want.
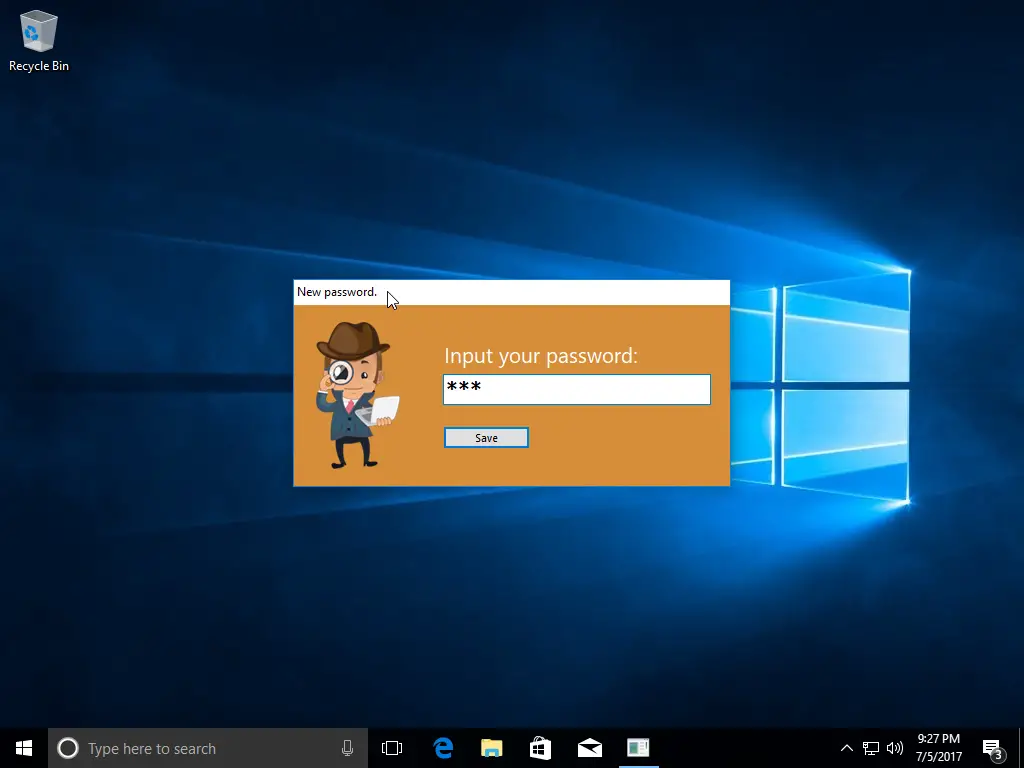
Password Protected
Let’s say you didn’t want to change “unhide” to something else, but you do want to password-protect the keylogger so that someone can’t change the options. Luckily that’s also available during the post-installation.
Reboot To Complete Installation
To complete the installation, you have to reboot your computer to complete the installation and adjust some additional settings. If you don’t reboot, you risk your target seeing what you were trying to do.
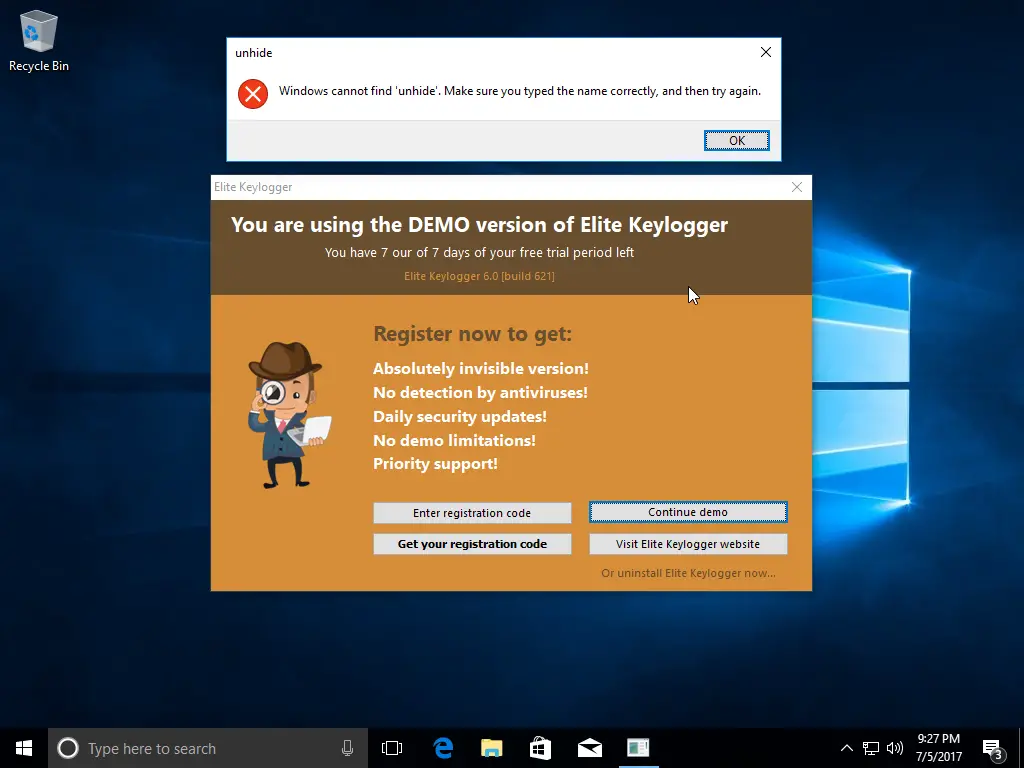
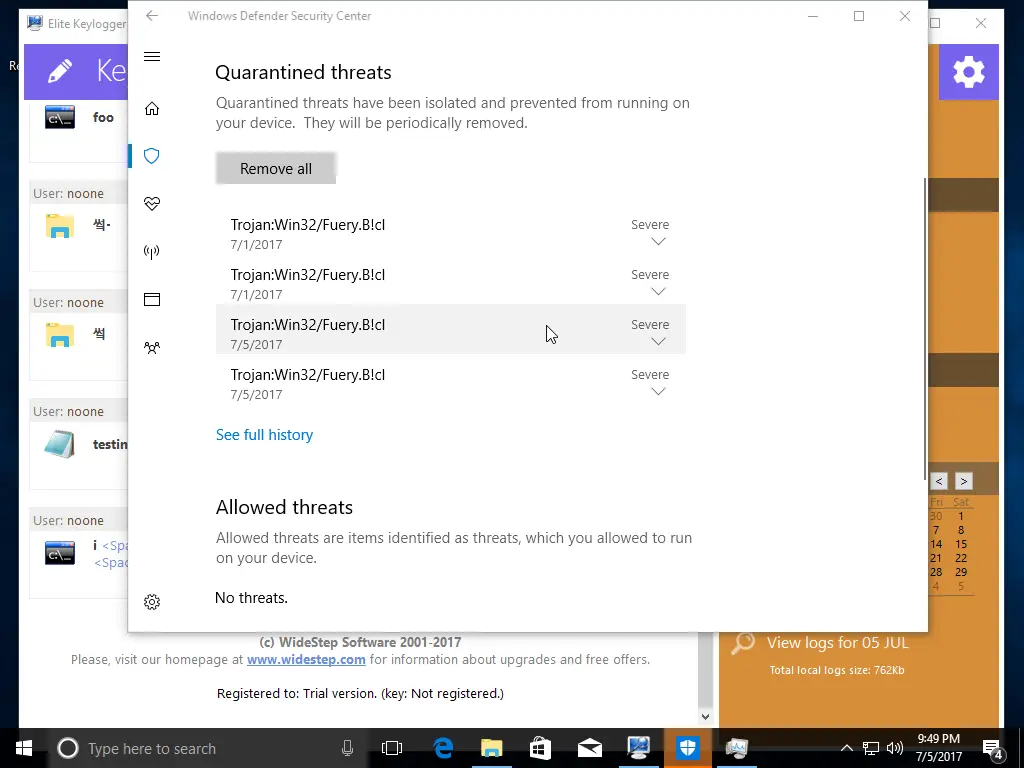
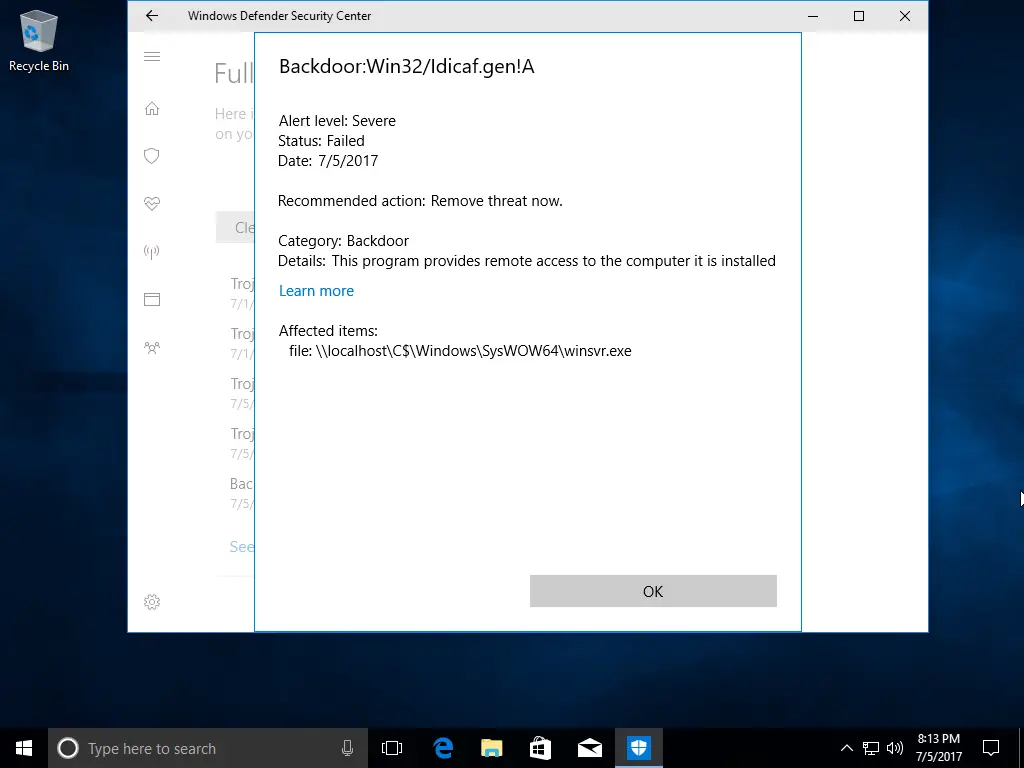
Unfortunately, after we rebooted, Windows Defender turned itself back on and found some pretty scary threats even though we “whitelisted” the keylogger. We’re unsure if these threats are the keylogger itself or the unnecessary download from mega.nz.
After your installation, you should probably clear the browsing history, so your target doesn’t see it. You should also remove anti-virus scans, so your target doesn’t find them.
Elite Keylogger Options And Settings
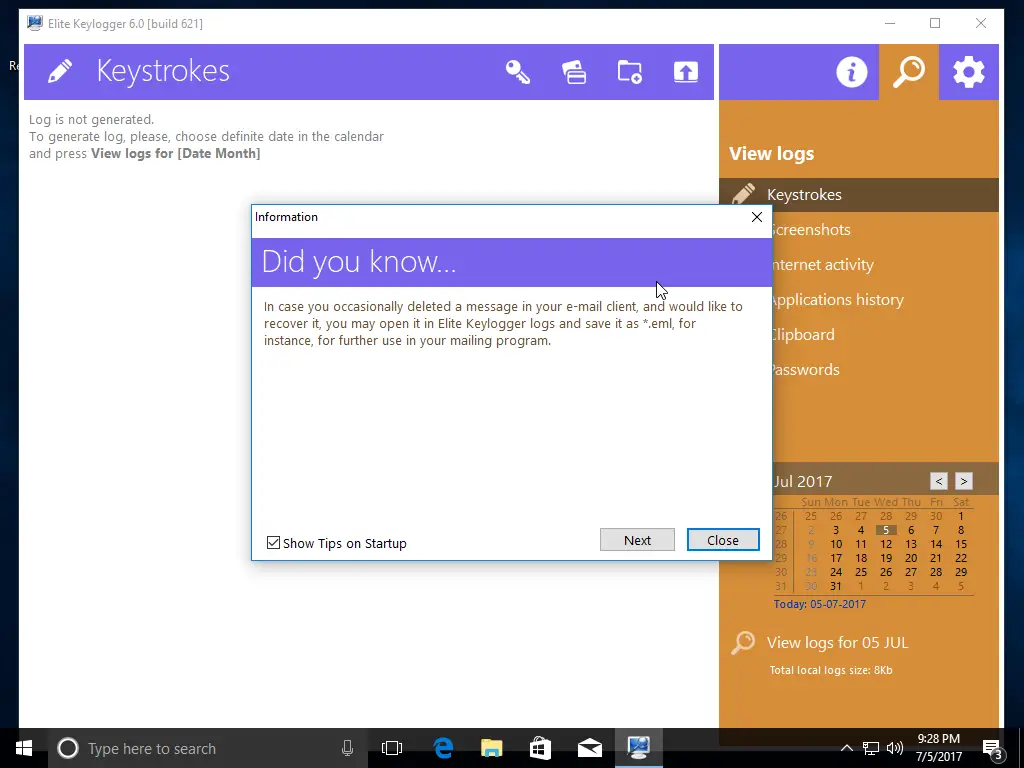
Once you have the software installed, you can start to see some of the things that it collects, including:
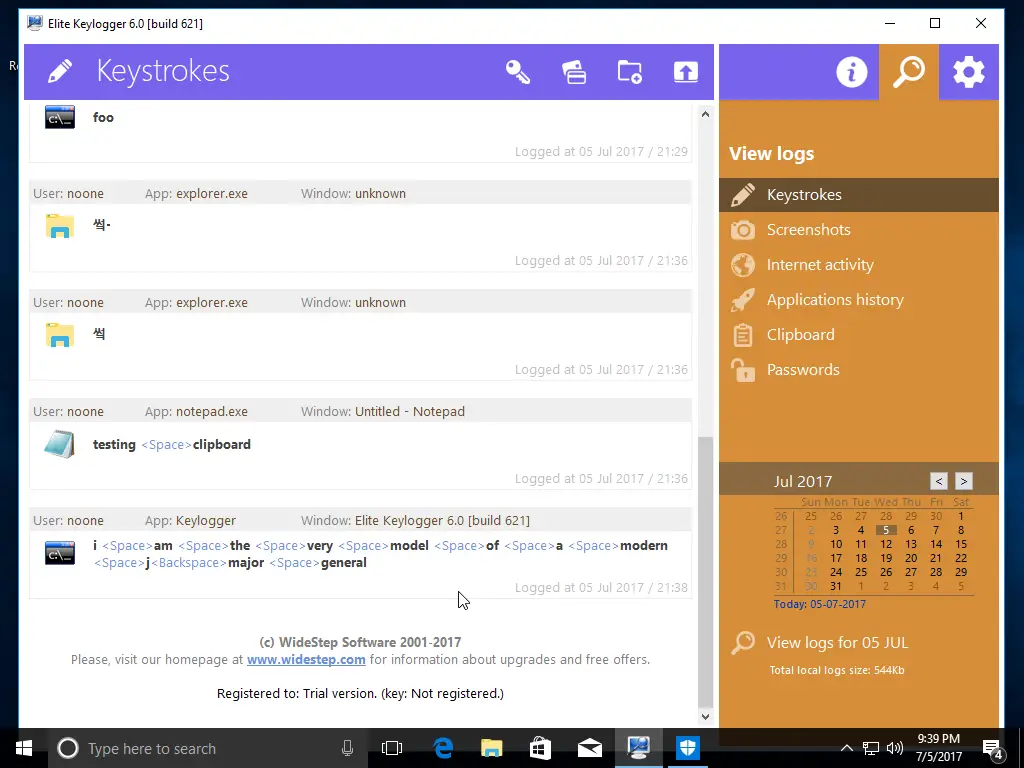
- Keystrokes
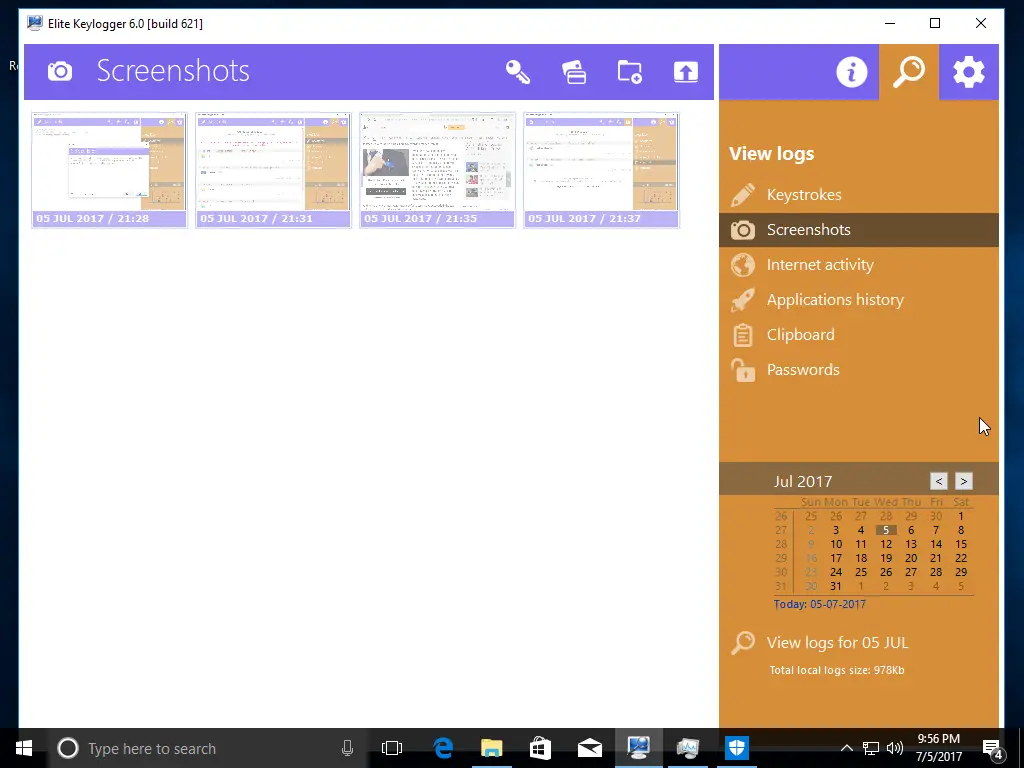
- Screenshots
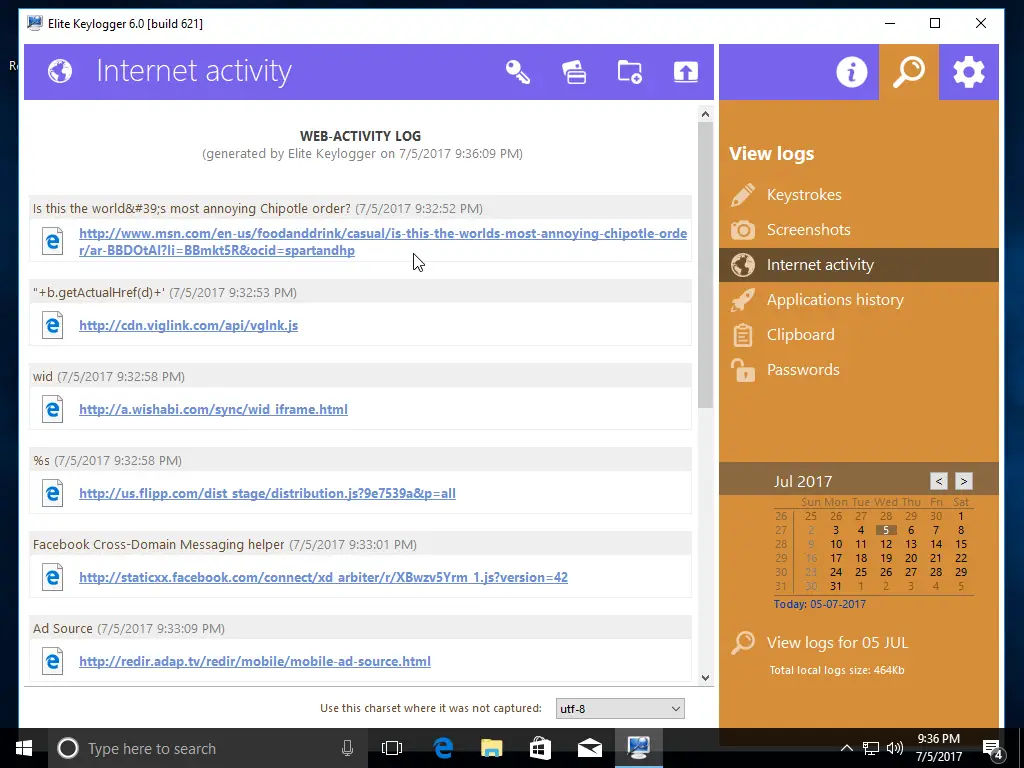
- Internet activity
- Applications history
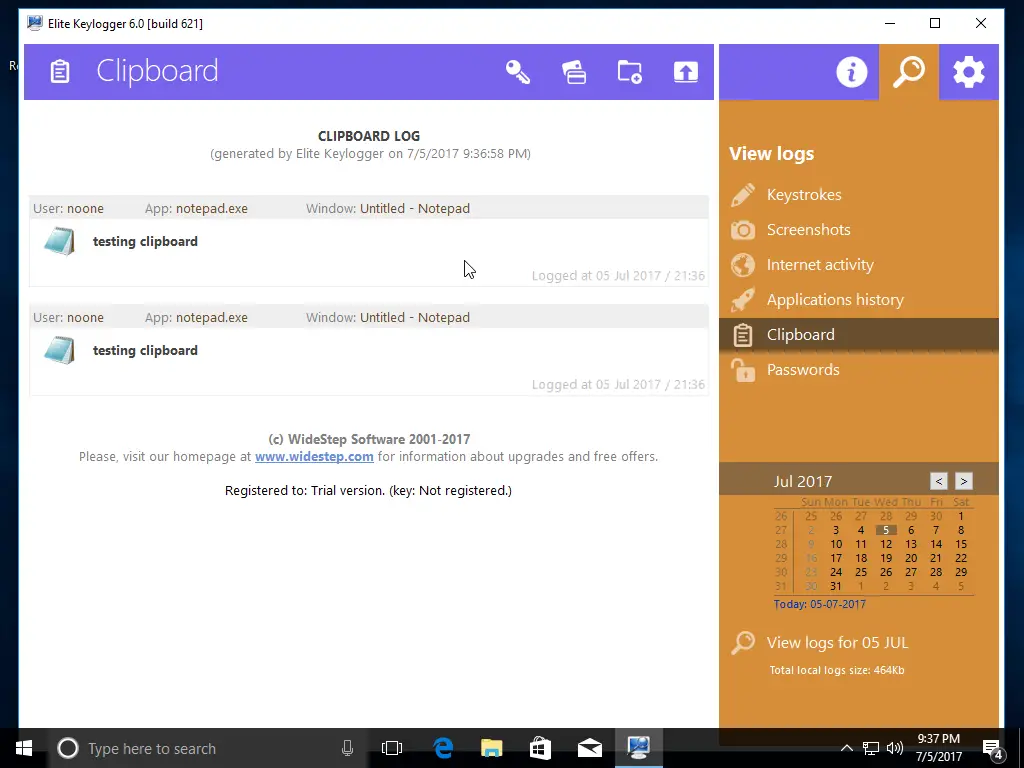
- Clipboard
- Passwords
Some options weren’t available in the demo, like password tracking, but after registration, you could view any passwords your target typed.
The interface has a calendar to select the dates you want to review.
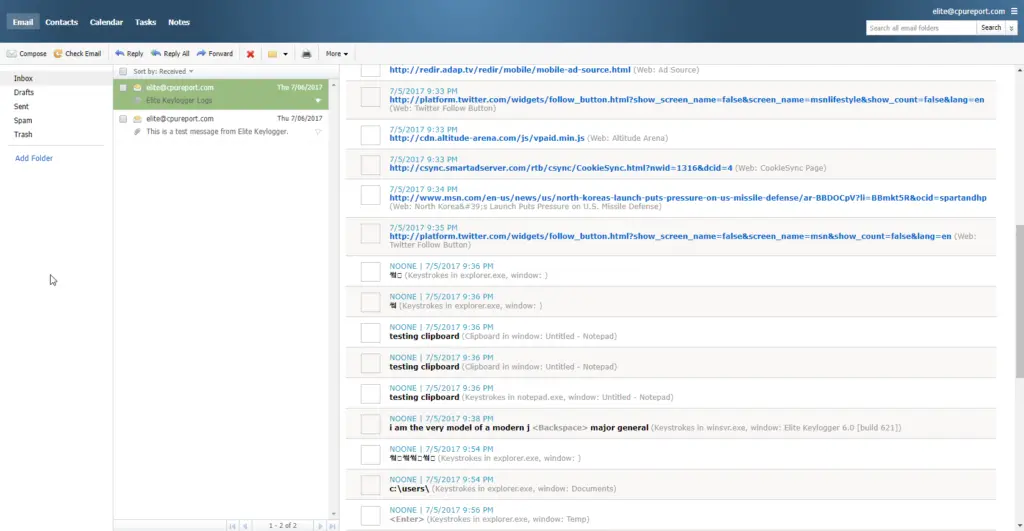
Remember that when your target is typing, it will monitor every keystroke, including any backspaces. You can see in our screenshot that we made a typo (on purpose, as far as you know), and it logged the backspace key.
If your target is typing a lot of text and doesn’t type very well, that could be a little difficult to read. Luckily there’s a screenshots tab that will take a snapshot every so often, so you can probably read what they were typing over there instead.
The Internet activity and Application history tabs are beneficial for seeing what apps and websites your target uses. Be aware that whenever you visit a website, it tends to download images, code, and other things from several websites you don’t usually notice. In our screenshot, you can see that it downloaded a JavaScript file from cdn.viglink.com. That’s a normal part of Internet browsing and doesn’t mean your target directly downloaded that file.
In the preferences area, you can export your preferences to install them on multiple computers, which might help set up monitoring on your small business or numerous kid computers.
Send Logs To Your Email
One of the excellent features of a keylogger is the ability to email the logs to yourself so that you don’t have to try to regain access to the computer when your target isn’t there. We tested the feature, and it worked well except for screenshots. They were too small to be helpful, but you probably get better images in the full version.
You can see that it sent us the logs from each area in the gallery screenshots below.
You can gather logs in several ways:
- FTP
- USB Drive
- Network Share
The trial version did not include the ability to see passwords, but the full version does. Be aware that email is inherently insecure so you could send your target’s bank or credit card password in plain text across the Internet to your mailbox. If that concerns you, you should consider another log option. We didn’t test FTP or USB.
The emailed logs included keystrokes, internet activity, application history, clipboard, and passwords. You can also send screenshots, but remember that an extended browsing session might create hundreds of images. If you’re going to send them to an email account, you should use a free Gmail account with lots of space.
Is It Really Hidden?
One of the most essential features of a keylogger is to ensure it remains hidden. We found out that the keylogger was installed during our reboot, though not fully configured, and Windows Defender could see it. We went further and tested a few more scenarios to see how much Windows Defender could see by running full scans. Ultimately we could configure it so that Windows Defender didn’t complain; however, it did alert us that items were skipped during the last scan. It talked about the whitelisted items we added, which might call attention to the files. But the files have cryptic names and look like typical Windows files, so a novice user probably won’t suspect anything.
There was no noticeable trace of the program in Task Manager or Services, which is good. We also looked at the MSCONFIG tool to see if we could find it and did not.
We were able to find the location where the screenshots were stored; however, most people don’t go poking around that deep into their computers, so it’s unlikely they would find them.
Note that the full version of the software may have a way to hide better from your anti-virus software. We were only reviewing the 7-day trial.
Gallery

Summary
There were several warnings about making sure that you disabled your anti-virus software so that the keylogger software would install properly. This might be difficult for some people as most users buy an anti-virus software package, install it, and forget about it until it tells them to reboot to apply updates. Most users don’t actively disable their anti-virus, which might be challenging for some non-technical users.
But once you get past the anti-virus issues, the tool works as expected and had several options for recording information and sending it to you for review.